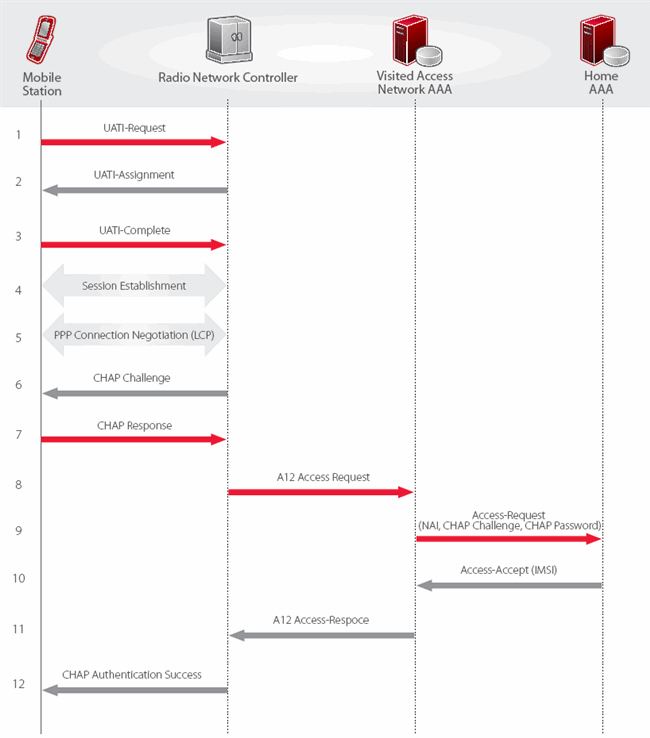
A12 Authentication (Access Authentication for EV-DO) is a CHAP-based mechanism used by a CDMA2000 Access Network (AN) to authenticate a 1xEV-DO Access Terminal (AT). A12 authentication occurs when an AT first attempts to access the AN and is repeated after some authentication timeout period. The element in the AN that performs this authentication is the Radio Network Controller (RNC) using its Access Network AAA (AN-AAA). In order to support A12 authentication, matching A12 credentials (i.e., an A12 Network Address Identifier (NAI) and A12 CHAP key) must be provisioned into the AT and the user’s home AAA server. Since these credentials are only shared between the AT and its home AAA, the AN-AAA forwards A12 challenge responses received from an AT to its home AAA to determine whether they are correct. A12 authentication is separate from packet data authentication that may occur later when a data session is being established.
A12 authentication is important for roaming since all participating operators in the IRT have agreed to support it. If A12 credentials are not provisioned into an AT, that AT will not be able to access any visited network that performs A12 authentication. In addition, the Mobile Node Identifier (MN ID) is obtained from the AN-AAA during successful A12 authentication. This MN ID is used by the AN on the A8/A9 and A10/A11 interfaces to enable handoffs of Packet Data Serving Node (PDSN) packet data sessions between ANs and between 1xEV-DO and 1xRTT systems. If A12 authentication is not performed, the MN ID must be somehow derived and such handoffs may not be possible without establishing a new Point-to-Point Protocol (PPP) session.
A12 authentication is defined in TIA-878 (3GPP2 A.S0008).
For information about A12 authentication in roaming, see CDG Reference Document #136.