A hotspot is a physical location that offers Internet access over a wireless local area network (WLAN) through the use of a router connected to a link to an Internet service provider. Hotspots typically use Wi-Fi technology. Hotspots may be found in coffe
History
Public park in Brooklyn, New York, has free Wi-Fi from a local corporation
Public access wireless local area networks (LANs) were first proposed by Henrik Sjödin at the NetWorld+Interop conference in The Moscone Center in San Francisco in August 1993. Sjödin did not use the term hotspot but referred to publicly accessible wireless LANs.
The first commercial venture to attempt to create a public local area access network was a firm founded in Richardson, Texas known as PLANCOM (Public Local Area Network Communications). The founders of that venture, Mark Goode, Greg Jackson, and Brett Stewart dissolved the firm in 1998, while Goode and Jackson created MobileStar Networks. The firm was one of the first to sign such public access locations as Starbucks, American Airlines, and Hilton Hotels. The company was sold to Deutsche Telecom in 2001, who then converted the name of the firm into "T-Mobile Hotspot." It was then that the term "hotspot" entered the popular vernacular as a reference to a location where a publicly accessible wireless LAN is available.
Uses
The public can use a laptop or other suitable portable device to access the wireless connection (usually Wi-Fi) provided. Of the estimated 150 million laptops, 14 million PDAs, and other emerging Wi-Fi devices sold per year for the last few years, most include the Wi-Fi feature.
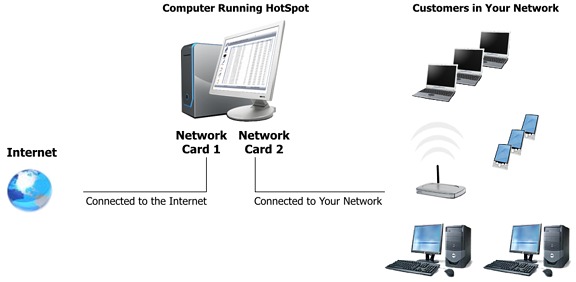
For venues that have broadband Internet access, offering wireless access is as simple as configuring one access point (AP), in conjunction with a router and connecting the AP to the Internet connection. A single wireless router combining these functions may suffice.
The iPass 2014 interactive map, that shows data provided by the analysts Maravedis Rethink, shows that in December 2014 there are 46,000,000 hotspots worldwide and more than 22,000,000 roamable hotspots. More than 10,900 hotspots are on trains, planes and airports (Wi-Fi in motion) and more than 8,500,000 are "branded" hotspots (retail, cafés, hotels). The region with the largest number of public hotspots is Europe, followed by North America and Asia.
Security
Security is a serious concern in connection with Hotspots. There are three possible attack vectors. First, there is the wireless connection between the client and the access point. This needs to be encrypted, so that the connection cannot be eavesdropped or attacked by a man-in-the-middle-attack. Second, there is the Hotspot itself. The WLAN encryption ends at the interface, then travels its network stack unencrypted and then travels over the wired connection up to the BRAS of the ISP. Third, there is the connection from the Access Point to the BRAS of the ISP. ...
The safest method when accessing the Internet over a Hotspot, with unknown security measures, is end-to-end encryption. Examples of strong end-to-end encryption are HTTPS and SSH.
Locations
Hotspots are often found at airports, bookstores, coffee shops, department stores, fuel stations, hotels, hospitals, libraries, public pay phones, restaurants, RV parks and campgrounds, supermarkets, train stations, and other public places. Additionally, many schools and universities have wireless networks in their campuses.
ABI Research reported there was a total of 4.9 million global Wi-Fi hotspots in 2012 and projected that number would surpass 6.3 million by the end of 2013. The latest Wireless Broadband Alliance (WBA) Industry Report outlines a positive scenario for the Wi-Fi market: a steady annual increase from 5.2m public hotspots in 2012 to 10.5m public hotspots in 2018.
Types
Free hotspots operate in two ways:
- Using an open public network is the easiest way to create a free hotspot. All that is needed is a Wi-Fi router. Similarly, when users of private wireless routers turn off their authentication requirements, opening their connection, intentionally or not, they permit piggybacking (sharing) by anyone in range.
- Closed public networks use a HotSpot Management System to control access to hotspots. This software runs on the router itself or an external computer allowing operators to authorize only specific users to access the Internet. Providers of such hotspots often associate the free access with a menu, membership, or purchase limit. Operators may also limit each user's available bandwidth (upload and download speed) to ensure that everyone gets a good quality service. Often this is done through service-level agreements.
Commercial hotspots
A commercial hotspot may feature:
- A captive portal / login screen / splash page that users are redirected to for authentication and/or payment. The captive portal / splash page sometimes includes the social login buttons.
- A payment option using a credit card, iPass, PayPal, or another payment service (voucher-based Wi-Fi)
- A walled garden feature that allows free access to certain sites
- Service-oriented provisioning to allow for improved revenue
- Data analytics and data capture tools, to analyze and export data from Wi-Fi clients
Many services provide payment services to hotspot providers, for a monthly fee or commission from the end-user income. For example, Amazingports can be used to set up hotspots that intend to offer both fee-based and free internet access, and ZoneCD is a Linux distribution that provides payment services for hotspot providers who wish to deploy their own service.
Major airports and business hotels are more likely to charge for service, though most hotels provide free service to guests; and increasingly, small airports and airline lounges offer free service.. Retail shops, public venues and offices usually provide a free Wi-Fi SSID for their guests and visitors.
Roaming services are expanding among major hotspot service providers. With roaming service the users of a commercial provider can have access to other providers' hotspots, either free of charge or for extra fees, which users will usually be charged on an access-per-minute basis.
Software hotspots
Many Wi-Fi adapters built into or easily added to consumer computers and mobile devices include the functionality to operate as private or mobile hotspots, sometimes referred to as "mi-fi". The use of a private hotspot to enable other personal devices to access the WAN (usually but not always the Internet) is a form of bridging, and known as tethering. Manufacturers and firmware creators can enable this functionality in Wi-Fi devices on many Wi-Fi devices, depending upon the capabilities of the hardware, and most modern consumer operating systems, including Android, Apple OS X 10.6 and later,, Windows mobile, and Linux include features to support this. Additionally wireless chipset manufacturers such as Atheros, Broadcom, Intel and others, may add the capability for certain Wi-Fi NICs, usually used in a client role, to also be used for hotspot purposes. However, some service providers, such as AT&T, Sprint, and T-Mobile charge users for this service or prohibit and disconnect user connections if tethering is detected.
Third-party software vendors offer applications to allow users to operate their own hotspot, whether to access the Internet when on the go, share an existing connection, or extend the range of another hotspot. Third party implementations of software hotspots include:
- Antamedia HotSpot software
- Connectify Hotspot
- Jaze Hotspot Gateway by Jaze Networks
- Hot Spot Network Manager (HSNM)
- Virtual Router
- Tanaza
- Start Hotspot software
Hotspot 2.0
Hotspot 2.0, also known as HS2 and Wi-Fi Certified Passpoint, is an approach to public access Wi-Fi by the Wi-Fi Alliance. The idea is for mobile devices to automatically join a Wi-Fi subscriber service whenever the user enters a Hotspot 2.0 area, in order to provide better bandwidth and services-on-demand to end-users, while also alleviating mobile carrier infrastructure of traffic overheads.
Hotspot 2.0 is based on the IEEE 802.11u standard, which is a set of protocols published in 2011 to enable cellular-like roaming. If the device supports 802.11u and is subscribed to a Hotspot 2.0 service it will automatically connect and roam.
Supported handsets
Billing
EDCF User-Priority-List
| Net traffic | |||||||
|---|---|---|---|---|---|---|---|
| low | high | ||||||
| Audio | Video | Data | Audio | Video | Data | ||
| User needs | time-critical | 7 | 5 | 0 | 6 | 4 | 0 |
| not time-critical | - | - | 2 | - | - | 2 |
The so-called "User-Fairness-Model " is a dynamic billing model, which allows a volume-based billing, charged only by the amount of payload (data, video, audio). Moreover, the tariff is classified by net traffic and user needs (Pommer, p. 116ff).
If the net traffic increases, then the user has to pay the next higher tariff class. By the way the user is asked for if he still wishes the session also by a higher traffic class. Moreover, in time-critical applications (video, audio) a higher class fare is charged, than for non time-critical applications (such as reading Web pages, e-mail).
Tariff classes of the User-Fairness-Model
| Net traffic | |||
|---|---|---|---|
| low | high | ||
| User needs | time-critical | standard | exclusive |
| not time-critical | low priced | standard |
The "User-fairness model" can be implemented with the help of EDCF (IEEE 802.11e). A EDCF user priority list shares the traffic in 3 access categories (data, video, audio) and user priorities (UP) (Pommer, p. 117):
- Data [UP 0|2]
- Video [UP 5|4]
- Audio [UP 7|6]
See Service-oriented provisioning for viable implementations
Security concerns
Some hotspots authenticate users; however, this does not prevent users from viewing network traffic using packet sniffers.
Some vendors provide a download option that deploys WPA support. This conflicts with enterprise configurations that have solutions specific to their internal WLAN.
In order to provide robust security to hotspot users, the Wi-Fi Alliance is developing a new hotspot program that aims to encrypt hotspot traffic with WPA2 security. The program was scheduled to launch in the first half of 2012.
Legal concerns
See also: Legality of piggybacking
Depending upon the location, providers of public hotspot access may have legal obligations, related to privacy requirements and liability for use for unlawful purposes. In countries where the internet is regulated or freedom of speech more restricted, there may be requirements such as licensing, logging, or recording of user information. Concerns may also relate to child safety, and social issues such as exposure to objectionable content, protection against cyberbullying and illegal behaviours, and prevention of perpetration of such behaviors by hotspot users themselves.
European Union
- Data Retention Directive Hotspot owners must retain key user statistics for 12 months.
- Directive on Privacy and Electronic Communications
United Kingdom
- Data Protection Act 1998 The hotspot owner must retain individual's information within the confines of the law.
- Digital Economy Act 2010 Deals with, among other things, copyright infringement, and imposes fines of up to £250,000 for contravention.